About Me!¶

Hey! I’m Sarah Al Balooshi, a Computer Engineering graduate of University of Bahrain, an avid reader, a video game enthusiast, and a perpetual curiosity cat.
My Background¶
I was raised in Bahrain, but my mother would always say that my heart was set somewhere else since I was born in Dublin, Ireland. I like to think that I am a child of the world, and I’ve loved to travel throughout the years. Exploring new places, cultural and historical sites, and meeting people from all walks of life is what I love about life.
Being a Computer Engineering major has taught me the power of the ever-growing digital age we are now living in, and also gave me the skills that I have today to aspire to be one of the innovators that brings forth more and further revolutionizes the future of technology.
My Previous Work¶
Most of the work I have done so far has been a reflection of all my acquired knowledge throughout my academic and professional career. I have a special interest in Networking, Cybersecurity, Artificial Intelligence, Robotics, and programming as a whole. As well as utilizing the complete access and power of an operating system through my fluency in a couple of Linux distributions, which has helped me with working cross-platform in projects, as well as easily fall into working on personal projects and university projects on the Raspberry Pi.
Listed below is an example of my work in the form of my Computer Engineering Graduation Project:
Graduation Project: Interactive Intelligent Robot with Facial Recognition and Presentation Attack Detection Capabilities¶
In order to understand the idea behind this project (and to decipher the word-y title), I’ll have to provide some background information on my chosen topic. The inspiration for my proposal of this project was the desire to bridge the gap between my three interests: Cybersecurity, Artificial Intelligence and Robotics. I was able to do this through researching about the latest technology being developed in the world of Cybersecurity, which is how I learned about Presentation Attack Detection.
What is Presentation Attack Detection?¶
Presentation Attacks are spoofing attacks that aim to trick biometric security systems. An example of this would be wearing a mask that resembles another person to impersonate them and get through their security system. If you’re a fan of the Mission Impossible movie franchise, you’ve probably already seen this happen on the silver screen several times!
 |
|---|
| Ethan Hunt Presentation Attack in action |
Simply put with this analogy in mind, Presentation Attack Detection (PAD) is the ability for us to figure out that Ethan Hunt is impersonating someone else before he can break through our security!
How Did I Do It?¶
Through my research, I found that many of the PAD systems that were being developed were based on Deep Learning algorithms to harbor the power of Artificial Intelligence to tell apart real human faces from fake ones. With this in mind, I was able to do the same and programmed a Deep Learning algorithm in Python that would not only detect Presentation Attacks for security, but also be able to perform Facial Recognition to identify the real person. This was made in mind to be used for security in smart buildings and smart homes, as it can filter in authorized personnel and deny unauthorized and malicious attackers (Sorry, Ethan Hunt).
Below you can see the system design of my Deep Learning algorithm, which combines two trained models each for Facial Recognition and Presentation Attack Detection. My partner and I curated our own dataset of photos of her and I (That’s me in the chart!), and used them to train both models to our specifications.
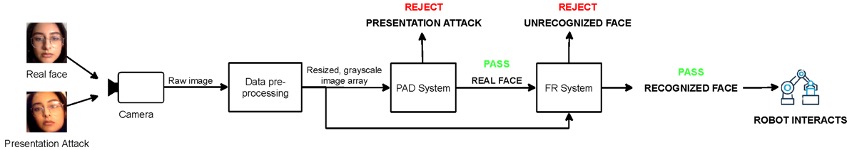 |
|---|
| The chart details the functionality of the algorithm |